Enterprise-Grade Cold Storage with Mathematical Guarantees
A robust long-term backup solution that combines AES-256-GCM encryption with Shamir's mathematically proven secret sharing. Protect your most critical assets—crypto wallets, SSH keys, passwords, and sensitive documents—with information-theoretic security designed for safe long-term storage.
Why Choose Fractum for Cold Storage
• Backup encryption master keys: Protect your backup infrastructure encryption keys
• Root CA private keys: Certificate authority and PKI infrastructure protection
• Emergency recovery credentials: Admin passwords, break-glass access credentials
• Password manager exports: LastPass, Bitwarden, KeePass backup files
• Legal & financial documents: Wills, contracts, tax records, insurance papers
• No single point of failure: Distributed trust across shares
• Share independence: Each share reveals zero information
• Bus Factor Protection: Write a Will and instructions for family members - they can pool shares to recover your assets
• Theft/Loss Protection: House fire, $5 wrench attack, or lost hardware wallet - shares remain secure
• Geographic distribution: Store shares across multiple locations (family, friends, safe deposit boxes)
• Shamir's Secret Sharing: Information-theoretic security
• Quantum-resistant: post-quantum algorithms
• Zero-knowledge property: K-1 shares reveal nothing
• GF(256) finite fields: Well-established algorithms
• FIPS 140-2 compatible: Uses compliant algorithms
• Deep dive into cryptographic implementation →
--network=none Docker guarantee• No telemetry or analytics: Your secrets never leave your environment
• Offline-first design: Works without internet connectivity
• No cloud dependencies: All operations run locally
• Memory protection: Secure deletion and swap prevention
• TEE compatible: Works with Trusted Execution Environments
• Non-root execution: Minimal privilege principles
• Reproducible builds: Cryptographic integrity verification
• Minimal dependencies: Reduced supply chain attack surface with few external libraries
• Cross-platform: Windows, macOS, Linux compatibility
• Comprehensive documentation: Security-first implementation guides
• Open source: Full transparency and community auditing
• Tested cryptographic implementations: Battle tested algorithm
How Fractum Transforms Cold Storage Operations
The Problem with Traditional Secret Storage
Most people store critical secrets in single points of failure—hardware wallets, password managers, or encrypted files hidden in one location. When these fail, get stolen, destroyed in a fire, or you simply forget where you hid them, your life savings or precious digital assets can be lost forever. Even having backups often means they're all in the same place or controlled by one person.
The Fractum Solution: Personal Security Through Distribution
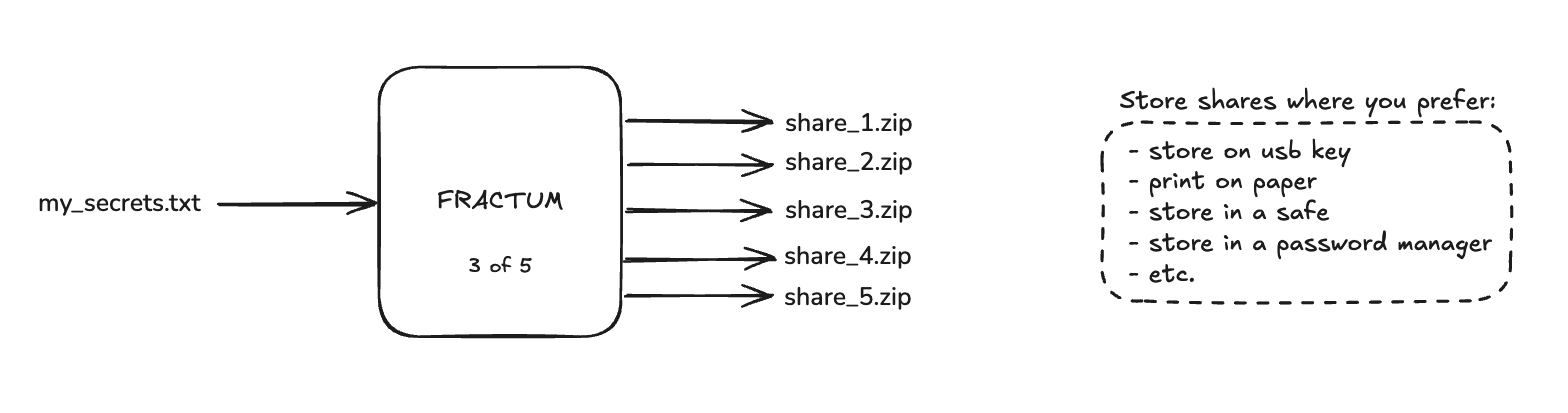
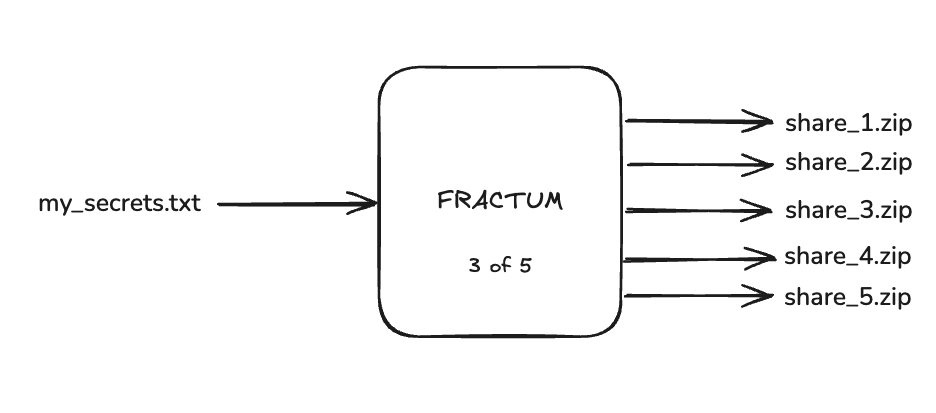
Fractum eliminates single points of failure through Shamir's Secret Sharing, providing information-theoretic security for your personal assets. Your secrets are split into shares where any K shares can reconstruct the original, but K-1 shares reveal absolutely nothing. Perfect for protecting crypto wallets, family passwords, and important documents from fire, theft, loss, or even coercion.
The Flow
Gather your Assets
- Crypto wallet seed phrases
- Backup encryption master keys
- Root CA private keys
- Emergency recovery credentials
- Password manager exports, etc.
Run Fractum
- AES-256-GCM encryption
- Shamir secret algorithm
- Threshold configuration
- Integrity verification
Store your Shares
- Encrypted payload
- Distributed shares
- Self-contained recovery
- Portable USB format
- Offline operation
Security Standards & Implementation
Cryptographic Standards
Battle-Tested Cryptography
- Shamir's Secret Sharing (SSS): Same algorithm used by Trezor (SLIP-39), Coinbase, Ledger Recover, and ICANN DNSSEC root key ceremonies
- AES-256-GCM: NSA Suite B approved, trusted by Signal, AWS, Google Cloud, and Apple for authenticated encryption
- Zero Novel Cryptography: Battle-tested primitives with decades of academic scrutiny and real-world deployment
- Fully offline: Portable CLI with no network dependencies
Industry Trust & Adoption
- NIST recommended: Key sizes and algorithms following NIST SP 800-175B
- Information-theoretic security: Mathematically proven protection
- Enterprise deployment: Used in financial services, research institutions, and cryptocurrency custody
- Open source transparency: Full code audit and verification capability
Get Started in Minutes
Fractum is designed for both security professionals and teams who need enterprise-grade cold storage without complexity. Choose your deployment strategy:
🐳 Docker Deployment
Enhanced security with complete network isolation. Perfect for production environments and security-conscious operations.
Start with Docker →⚙️ Manual Installation
Full control and flexibility for developers. Cross-platform support with comprehensive automation scripts.
Manual Setup →Key Takeaways
In Summary: What is Fractum?
Fractum is an enterprise-grade secret sharing tool that uses Shamir's Secret Sharing algorithm and AES-256-GCM encryption to split sensitive files into multiple encrypted shares. It's designed for cold storage and long-term backup of critical digital assets like cryptocurrency wallets, SSH keys, passwords, and important documents.
Core Benefits
• Information-theoretic security - mathematically proven protection
• No single point of failure - distributed trust across multiple shares
• Air-gapped operation - works completely offline for maximum security
• Threshold cryptography - configurable K-of-N security model
• Cross-platform support - Windows, macOS, and Linux compatibility
• Open source transparency - full community audit and verification
Perfect Use Cases
Fractum is ideal for: Cryptocurrency wallet backup, SSH key protection, password manager exports, backup encryption keys, root CA private keys, emergency recovery credentials, legal documents, and any sensitive data requiring long-term secure storage with distributed access control.
How It Works
Fractum encrypts your file with AES-256-GCM, then uses Shamir's Secret Sharing to split the encryption key into multiple shares. You can configure a threshold (e.g., 3-of-5 shares needed) for reconstruction. Individual shares reveal zero information about the original file, providing information-theoretic security.