How to Encrypt Files with Fractum¶
This comprehensive guide covers encrypting files using Fractum, including configuration options, command-line usage, Docker deployment, and security best practices.
Quick Summary¶
Fractum encryption process:
- Choose threshold settings (K shares needed out of N total shares)
- Run encryption command (interactive or command-line mode)
- Distribute encrypted shares to trusted custodians immediately
- Verify successful encryption before destroying original
Encryption typically takes 30 seconds to 2 minutes depending on file size.
Prerequisites Checklist¶
Before encrypting files with Fractum, ensure you have:
✅ Fractum properly installed (manual installation or Docker setup)
✅ File ready for encryption and accessible on your system
✅ Threshold decision made - how many shares needed (K) vs. total shares (N)
✅ Distribution plan - where you'll store each share securely
✅ Security review - read share distribution security guidelines
Important: Avoid keeping shares gathered on the same machine for extended periods.
Encryption Methods¶
Interactive Mode (Beginner-Friendly)¶
Interactive mode guides you through the entire process:
The interactive mode provides:
- Step-by-step operation selection (encrypt/decrypt)
- Guided configuration with explanations
- Real-time validation of your choices
Perfect for: First-time users, learning the process, or when you want guided assistance.
Command Line Mode (Advanced Users)¶
For experienced users and automation, use direct command-line encryption:
Expected output:
Using label: my_passwords (spaces replaced with underscores)
Using existing shares directory
Generated share set ID: 086affead7924664
Generated shares: 5
Encrypted file: MY_FILE.txt.enc
Created archive: /Users/alice/my_repos/fractum/shares/share_1_2.zip
Created archive: /Users/alice/my_repos/fractum/shares/share_2_2.zip
Created archive: /Users/alice/my_repos/fractum/shares/share_3_2.zip
Created archive: /Users/alice/my_repos/fractum/shares/share_4_2.zip
Created archive: /Users/alice/my_repos/fractum/shares/share_5_2.zip
Step 1: Prepare your file
Step 2: Run encryption with network isolation
docker run --rm -it \
--network=none \
-v "$(pwd)/data:/data" \
-v "$(pwd)/shares:/app/shares" \
fractum-secure encrypt /data/MY_FILE.txt \
--threshold 3 \
--shares 5 \
--label "my passwords" \
-v
Expected output:
Using label: my_passwords
Using existing shares directory
Generated share set ID: 086affead7924664
Generated shares: 5
Encrypted file: /data/MY_FILE.txt.enc
Created archive: /app/shares/share_1.zip
Created archive: /app/shares/share_2.zip
Created archive: /app/shares/share_3.zip
Created archive: /app/shares/share_4.zip
Created archive: /app/shares/share_5.zip
Configuration Options Explained¶
Understanding Threshold and Shares¶
Key concepts:
- Threshold (K): Minimum number of shares required to decrypt the file
- Total Shares (N): Total number of shares to generate
- Mathematical rule: K ≤ N ≤ 255
Common configuration patterns:
| Configuration | Security Level | Use Case | Recovery Difficulty |
|---|---|---|---|
| K=2, N=3 | Basic | Personal backup | Easy |
| K=3, N=5 | Balanced | Family/small team | Moderate |
| K=5, N=8 | High | Organization | Moderate-Hard |
| K=7, N=10 | Maximum | Enterprise/critical | Hard |
Choosing the right settings:
- Lower K: Easier recovery but less security
- Higher N-K difference: Better protection against share loss
- Consider custodian availability: Don't set K higher than available trusted parties
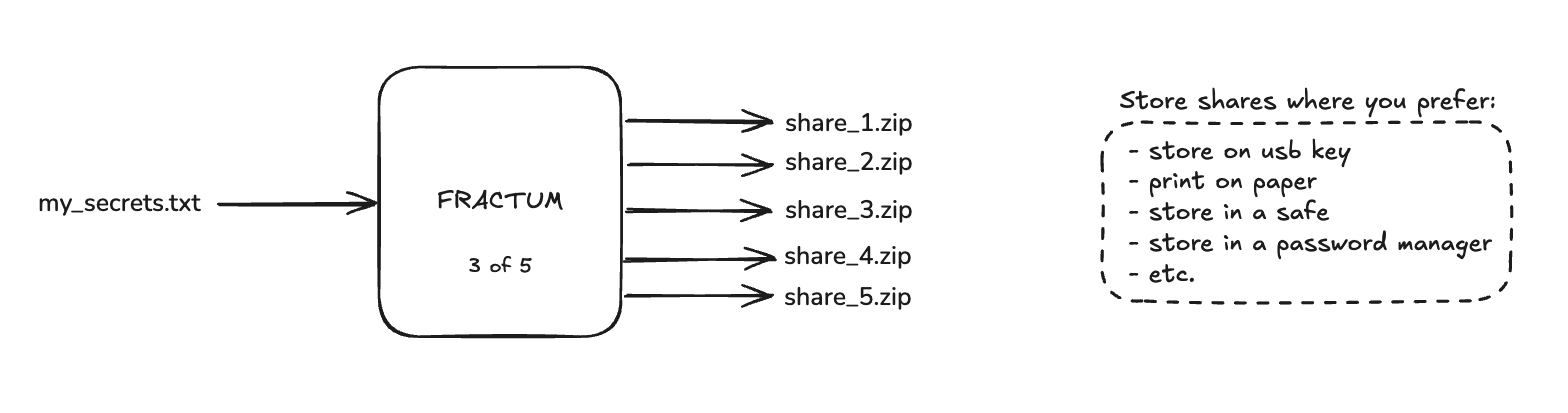
Output Structure After Encryption¶
Fractum creates this file structure:
current_directory/
├── MY_FILE.txt.enc # AES-256-GCM encrypted file
└── shares/ # Shares directory
├── share_1.zip # Share archive 1 (portable bundle)
├── share_2.zip # Share archive 2 (portable bundle)
├── share_3.zip # Share archive 3 (portable bundle)
├── share_4.zip # Share archive 4 (portable bundle)
└── share_5.zip # Share archive 5 (portable bundle)
Each share ZIP archive contains: - Share data file (share_N.txt) - contains cryptographic share + metadata - Complete portable software - self-contained Fractum that fits on USB
Understanding Share Content¶
Each share file contains critical information:
{
"share_index": 2,
"share_key": "ADmi79NiutDoE2Iulgn8Q+YtOcdU/UbSo4C9LPUINJ4=", # the acutal cryptographic share key
"label": "my passwords",
"share_integrity_hash": "d5201c0d817c9960182aeda0f9abeb98c7c81dff99e8268c602739a851086cc0",
"threshold": 3,
"total_shares": 5,
"tool_integrity": { ... },
"python_version": "3.12.10",
"share_set_id": "41ded860ae32a908"
}
Critical values for recovery:
share_index: Unique identifier for this specific shareshare_key: Base64-encoded cryptographic share valuethreshold: Minimum shares needed (K value)total_shares: Total shares created (N value)
For physical storage: You can extract and print these values for manual share entry mode.
Best Practices for Encryption¶
- Choose appropriate K and N values based on your security requirements
- Use descriptive but secure labels for your encrypted files
- Immediately distribute shares to separate locations after encryption
- Verify the encryption completed successfully before distributing shares
- Document your threshold settings for future reference
- Test recovery with a non-sensitive file first
Security Guarantees¶
Fractum provides these cryptographic guarantees:
✅ Memory security: Automatic clearing of sensitive data from RAM
✅ No temporary files: No unencrypted data written to disk during process
✅ Cryptographically secure randomness: Uses OS-provided entropy sources
✅ Unique key derivation: Each encryption uses fresh random data
✅ Information-theoretic security: K-1 shares reveal zero information
Verification Steps¶
After encryption, verify success:
- Check share count: Verify N share files were created
- Inspect file sizes: Shares (.txt file inside the zip file) should be small (few KB), encrypted file similar to original
- Validate share integrity: Each share should contain valid JSON (.txt file)
- Test partial reconstruction: Optional - verify K shares can decrypt (with test data)
Key Takeaways¶
In summary, Fractum file encryption:
✅ Uses AES-256-GCM encryption combined with Shamir's Secret Sharing
✅ Creates portable share bundles that work independently
✅ Provides configurable threshold security (K-of-N model)
✅ Works offline for air-gapped security environments
✅ Generates self-contained archives for easy distribution
✅ Ensures information-theoretic security with mathematical guarantees
Perfect for: Cryptocurrency wallets, SSH keys, password databases, critical documents, and any sensitive data requiring distributed access control.
Next steps: Learn about decrypting files using shares and review security best practices.